"I was gonna make a really cool challenge, but then I literally forgot about it, so all I have is this blank image. Good luck!"
This message suggested that while the image might look empty, valuable data could be concealed inside, making this a classic steganography challenge.
Approach and Solution
To analyse the image, I used my favourite online tool: Aperisolve. It’s a powerful web-based utility that automates various steganography and forensics tools, saving me time and effort compared to running each tool manually.
After uploading the image, Aperisolve ran several tools under the hood, such as:
- Zsteg
- Binwalk
- Steghide
- Exiftool
- Strings analysis
The Zsteg output was particularly revealing. It showed several pieces of data hidden in different colour channels and bit layers of the image. One of the lines directly revealed the flag:
| b1,a,lsb,xy .. text: "CIT{n1F0Rsm0Er40}"
b1,bgr,msb,xy .. file: PGP Secret Sub-key - b2,abgr,lsb,xy .. text: "-6k^6\n<^G" b3,a,lsb,xy .. file: StarOffice Gallery theme \002\001\004\020@\004\222\011\004\202Hs b3,rgb,msb,xy .. text: "x&f{KH:7" b3,bgr,lsb,xy .. text: "AJ~HJ2oS" b4,a,lsb,xy .. file: TeX font metric data (\001) b4,rgba,lsb,xy .. text: "@2AXqmPv1" |
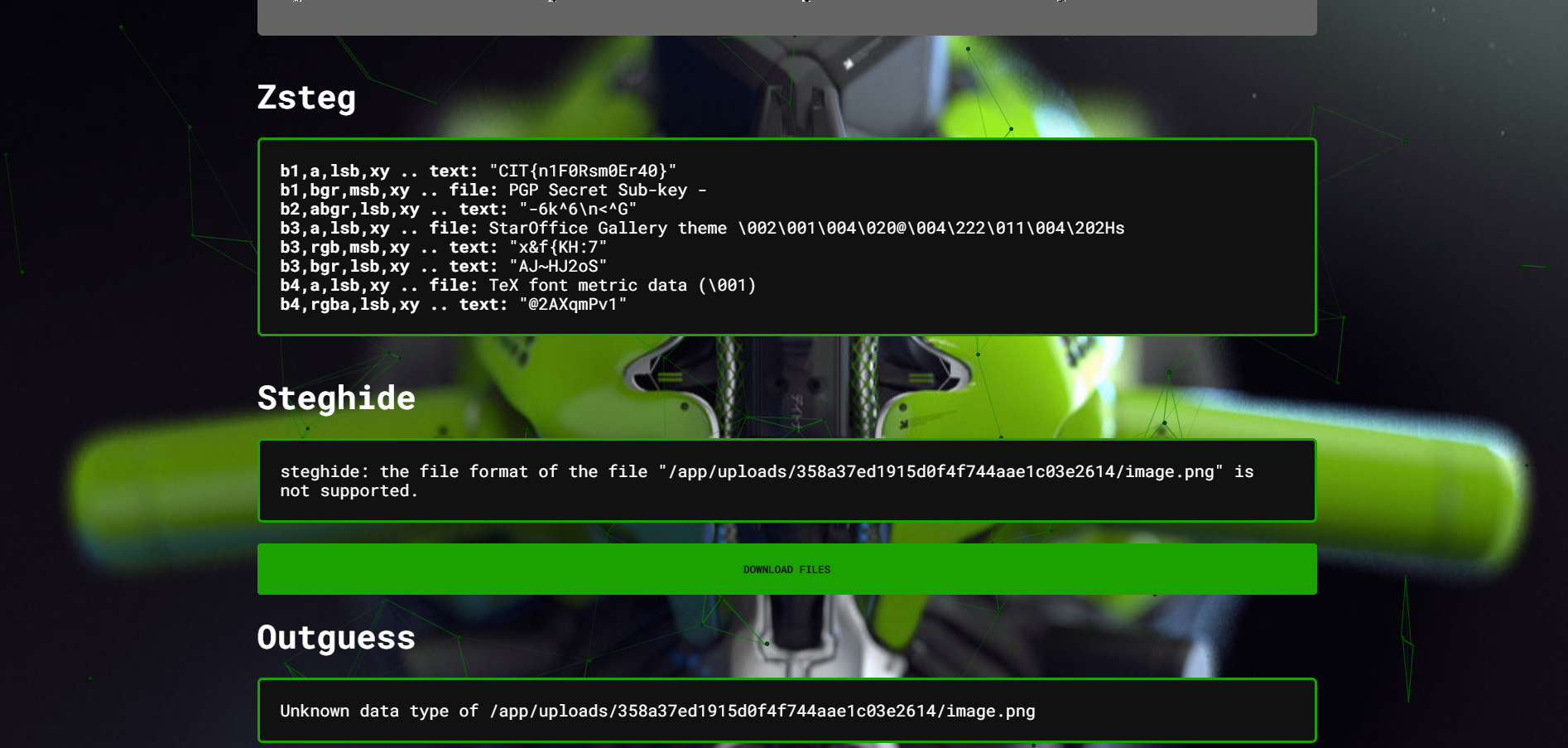
Although other embedded data (like file headers and scrambled text) was detected, this clear line gave the correct flag for the challenge.
Conclusion
The Blank Image challenge from CTF@CIT 2025 may have seemed simple at first glance, but it cleverly hid data in the image’s least significant bits. Thanks to Aperisolve and tools like Zsteg, I was able to uncover the flag without diving into tedious manual analysis. This write-up highlights the importance of steganographic techniques in cybersecurity and how even a "blank" file can carry secrets.