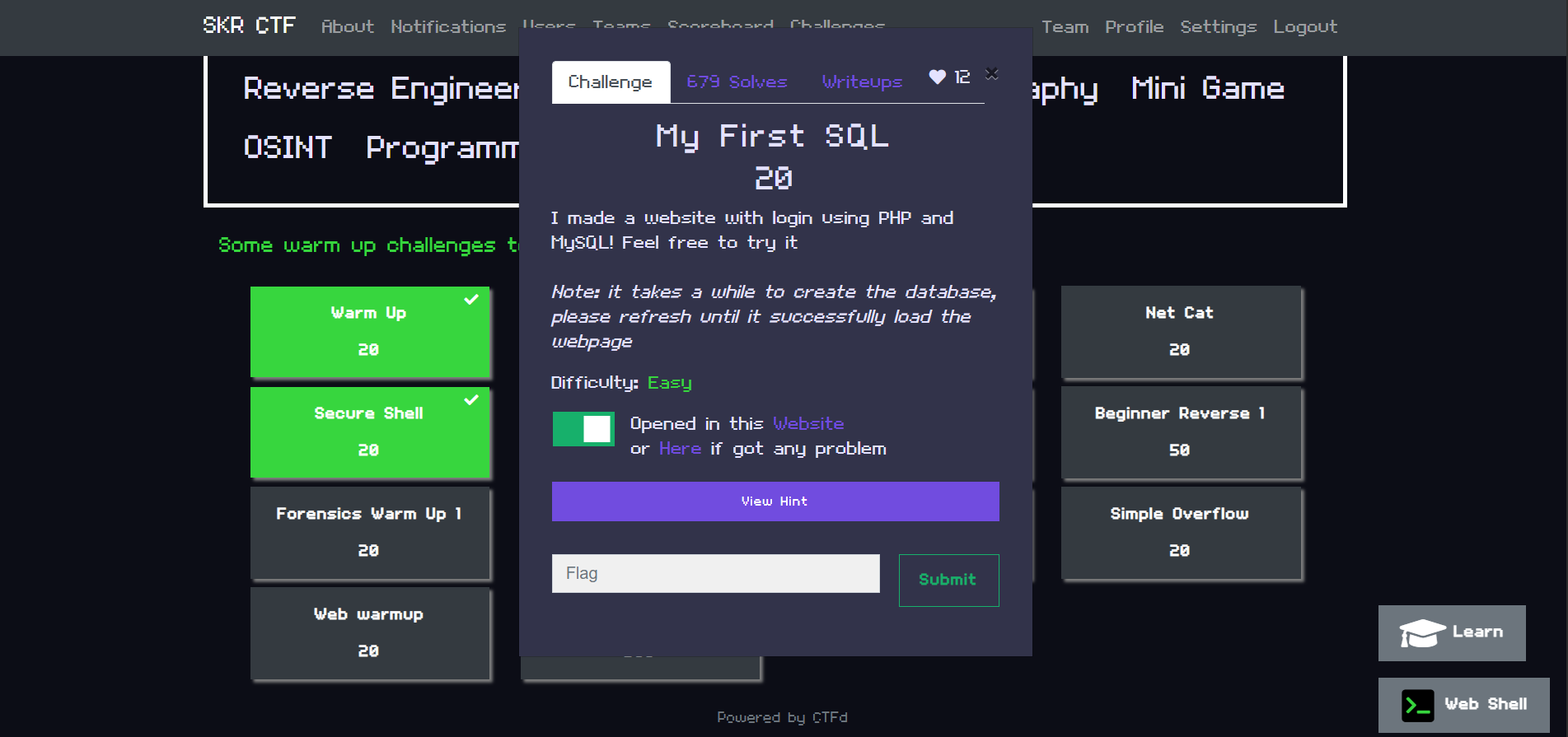
Challenge Overview
Descriptions: I made a website with login using PHP and MySQL! Feel free to try it
Note: it takes a while to create the database, please refresh until it successfully load the webpage.
Difficulty: Easy
Challenge Link: https://skrctf.me/challenges#My%20First%20SQL
Exploitation Strategy
Step 1: Upon loading the webpage, the content appears minimal, with no obvious clues or visible flags. But I can see a login page, and in the challenge descriptions mention "MySQL" which means we might need to do some SQL Injections.

Step 2: I found that it required you to fill up the "email" and "password" fields.
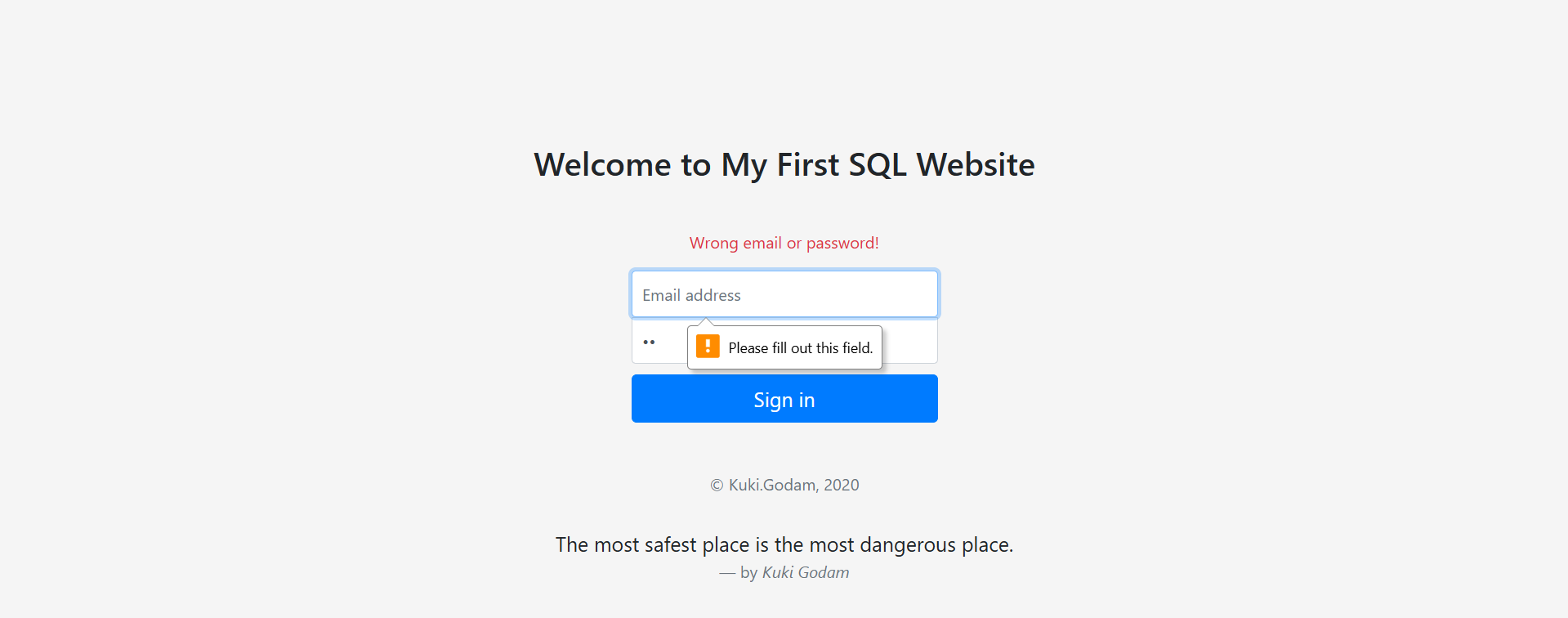
Step 3: After that, I tried the possible injection.
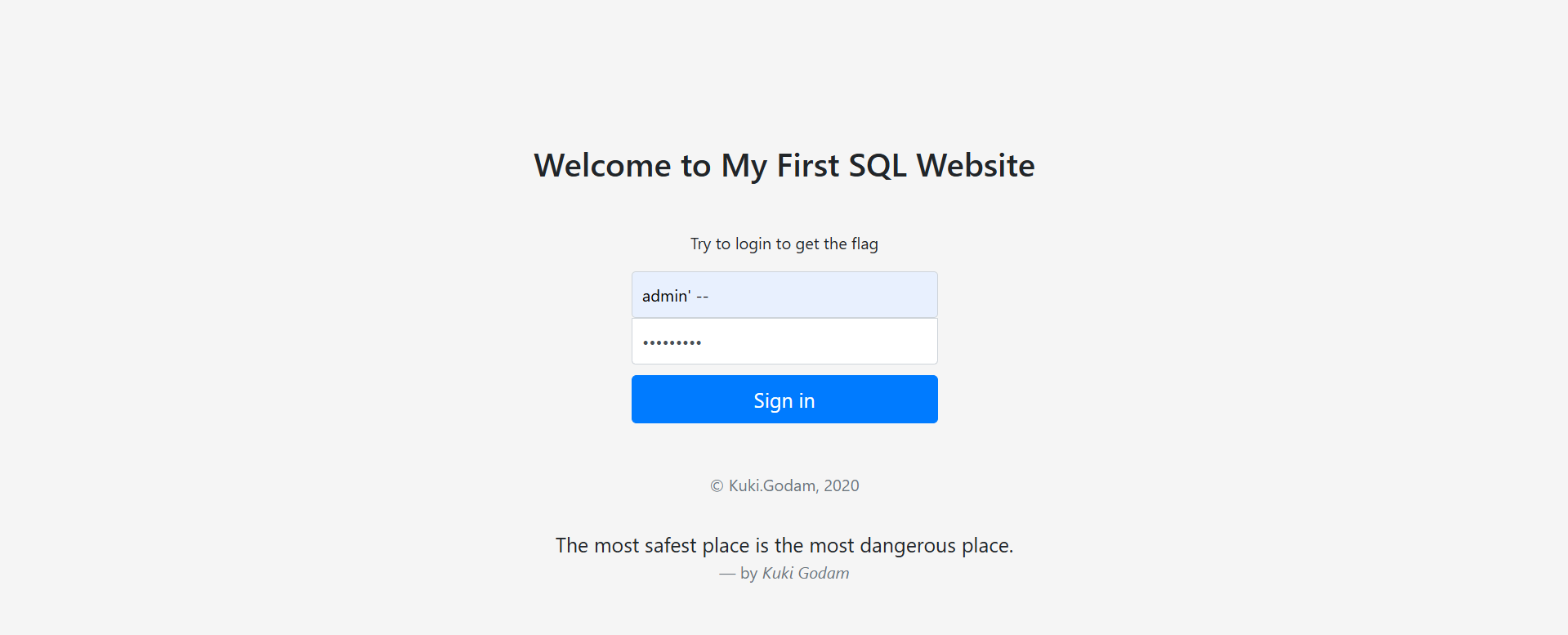
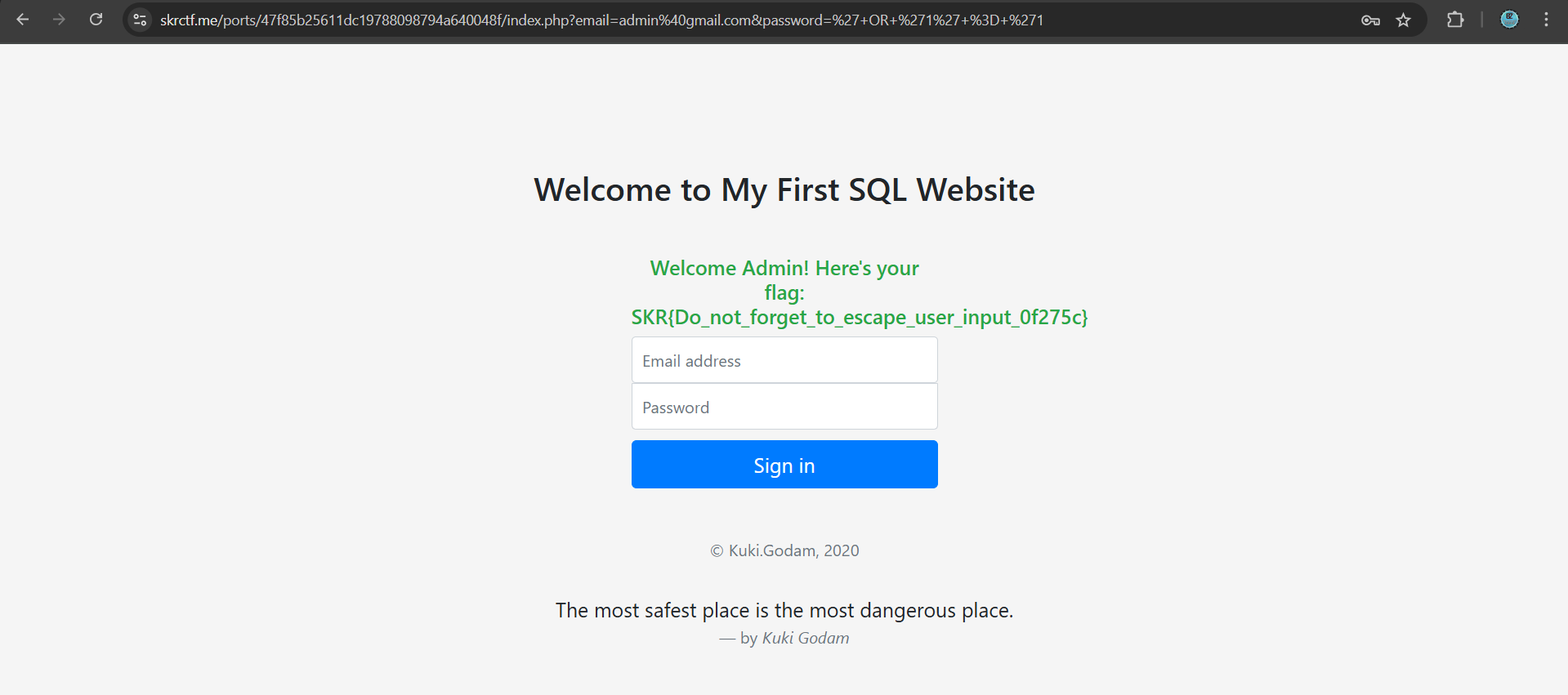
Step 4: Finally, the correct payload to inject is
and the Flag is "SKR{Do_not_forget_to_escape_user_input_0f275c}"
| ' OR '1' = '1 |
In summary, the "My First SQL" challenge from the SKRCTF series serves as an excellent introduction to SQL injection (SQLi) vulnerabilities. By exploiting a basic SQLi flaw in a PHP-MySQL login system, participants learn how improper input handling can compromise web application security. This challenge underscores the importance of input validation and the use of parameterized queries to prevent such vulnerabilities. For those new to web security, this exercise provides a practical foundation for understanding and identifying common security flaws.